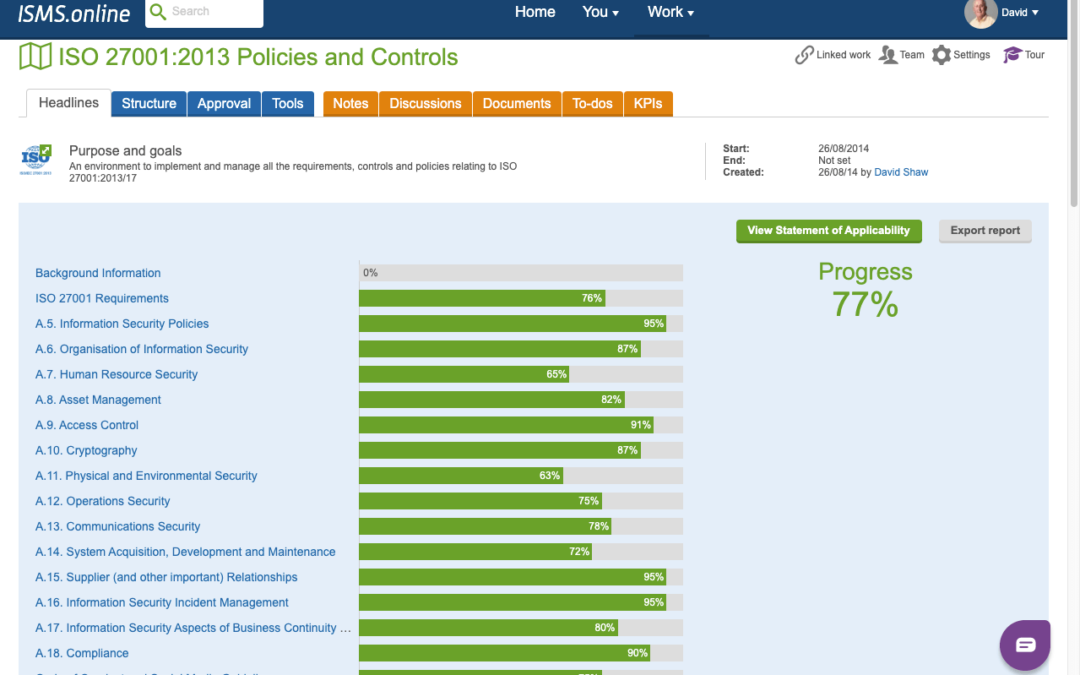
Unveiling the Efficiency of ISMS.online
In the fast-evolving landscape of information security management, ISMS.online stands as a beacon, offering a cloud-based solution tailored for organisations striving to achieve and maintain ISO27001 certification. In collaboration with Resilient IiT, this comprehensive platform streamlines every facet of the ISO27001 process, ensuring efficiency, compliance, and best practices.
Key Features of ISMS.online
- Comprehensive ISMS Framework
ISMS.online presents a pre-configured framework aligning with ISO27001 requirements, providing a clear path to certification. - Policy Management Module
Effortlessly create, review, approve, and publish policies and procedures using templates and guidance. - Risk Management Module
Identify, analyse, evaluate, and treat risks using various methodologies and tools, fostering a proactive security stance. - Incident Management Module
Facilitate the reporting, investigating, and resolvinginvestigation, and resolution of of information security incidents and breaches. - Audit Management Module
Supports planning, execution, and reporting of internal and external audits, alongside corrective and preventive actions. - Dashboard and Reporting Module
Real-time overview of ISMS performance, progress, customisablecustomizable reports, and analytics. - Collaboration and Communication Module
Share information, documents, and feedback with stakeholders while accessing online support and training.
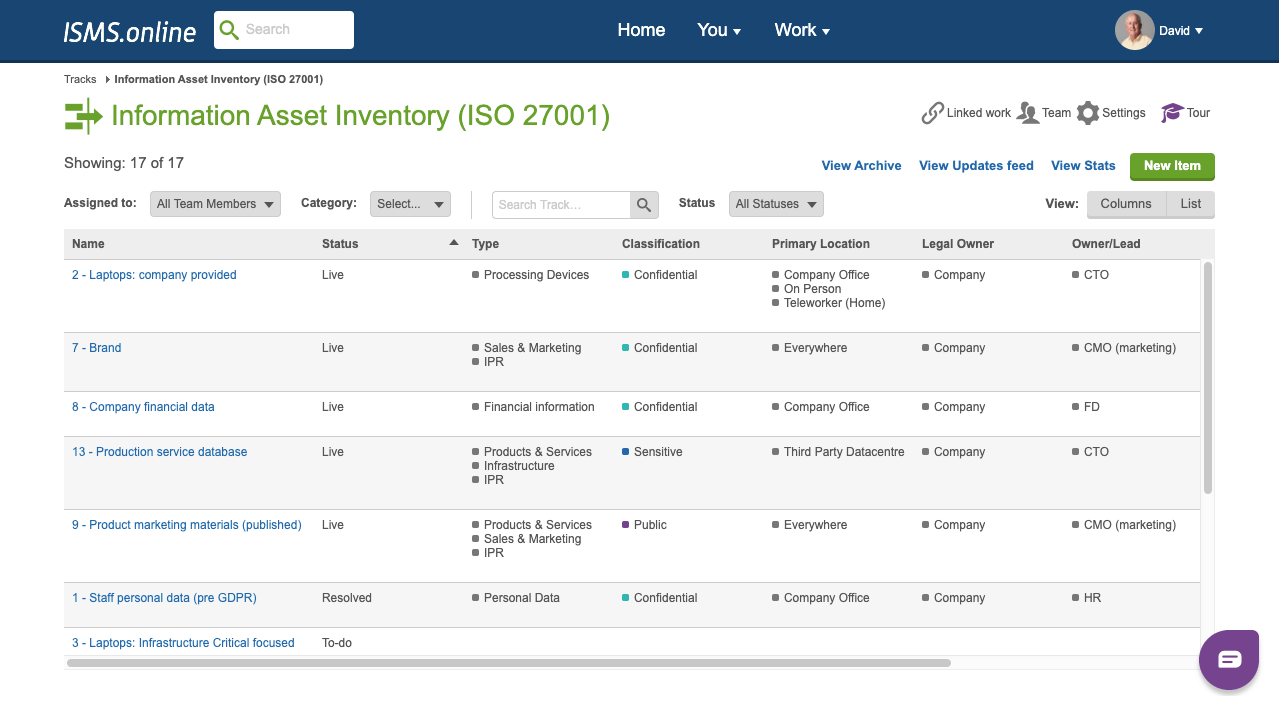
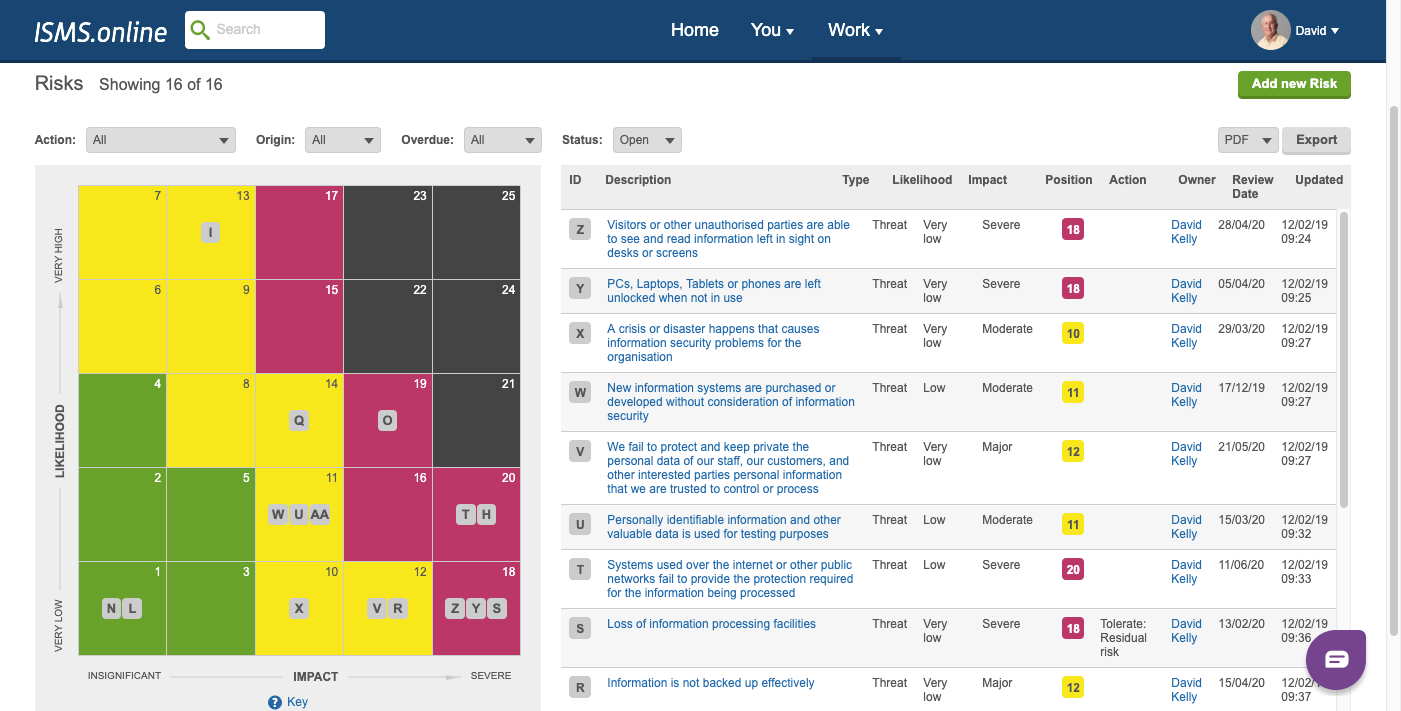 Benefits of ISMS.online
Benefits of ISMS.online
- Reduced Costs and Complexity:
Eliminate the need for multiple tools, reducing overhead and maintenance costs. A structured approach minimises the risk of errors and omissions. - Improved Efficiency and Effectiveness:
Automation and streamlining saves time and effort, enhancing the quality and consistency of information security management. - Increased Visibility and Accountability:
Provide users and managers with with a comprehensive view of ISMS status, fostering transparency, and accountability.
Why Choose ISMS.online
Trusted by over 500 organisations, ISMS.online suitsis suitable for entities of any size and sector. It offers customisationcustomization to meet specific needs, adheres to the highest data protection and privacy standards, and is hosted in the UK.
As a collaborative partner of Resilient IT, a leading provider of business continuity and information security consulting in New Zealand, ISMS.online has becomebecomes more than just a tool. Resilient IT offers implementation, management, and expert advice, supporting organisations throughout their ISO27001 journey.
In a world where information security is non-negotiable, ISMS.online by Resilient IT emerges as a powerful ally, simplifying the path to ISO27001 certification. With its user-friendly interface, robust features, and the backing of Resilient IT’s expertise, organisations can navigate the complex landscape of information security with confidence.
Elevate Security Measures with KnowBe4’s Cutting-Edge Solutions
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
Understanding SOC 2 Attestation For Robust Cybersecurity
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
Resilient IT: Your Path to ISO Certification
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
Understanding Phishing: Types, Identification and Avoidance Strategies
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
ISO27001:2022: What do the updates mean for you?
ISO/IEC 27001:2022 Update: What are the main changes and what does this mean for you? This year, the ISO27001 standard saw its first significant update since 2013. What, however, do these changes mean for your organisation’s security? Why has ISO27001:2022 changed? At...
Webinar: ISO 27001: What can Kiwis learn from one of the leading standards for information security?
With the increase of businesses moving to data-driven solutions comes the need for the implementation of information security best practises. Cue, ISO 27001. ISO 27001 is a globally recognised international standard focussed on information security management that...
Elevate Security Measures with KnowBe4’s Cutting-Edge Solutions
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
Understanding SOC 2 Attestation For Robust Cybersecurity
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
Resilient IT: Your Path to ISO Certification
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
Understanding Phishing: Types, Identification and Avoidance Strategies
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
ISO27001:2022: What do the updates mean for you?
ISO/IEC 27001:2022 Update: What are the main changes and what does this mean for you? This year, the ISO27001 standard saw its first significant update since 2013. What, however, do these changes mean for your organisation’s security? Why has ISO27001:2022 changed? At...
Webinar: ISO 27001: What can Kiwis learn from one of the leading standards for information security?
With the increase of businesses moving to data-driven solutions comes the need for the implementation of information security best practises. Cue, ISO 27001. ISO 27001 is a globally recognised international standard focussed on information security management that...
Elevate Security Measures with KnowBe4’s Cutting-Edge Solutions
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
Understanding SOC 2 Attestation For Robust Cybersecurity
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
Resilient IT: Your Path to ISO Certification
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
Understanding Phishing: Types, Identification and Avoidance Strategies
In the digital age, protecting personal and business information from malicious cyber threats has become increasingly crucial. One of the most common and pernicious tactics used by cybercriminals is phishing. Understanding what constitutes a phishing attack and how to identify and avoid them can be the difference between maintaining the integrity of your private information and falling prey to a damaging data breach.
What is Phishing?
Phishing is a form of social engineering scheme frequently employed to illicitly obtain user information, such as login details and credit card information. It transpires when a malicious actor, posing as a reputable source, tricks a target into accessing an email, instant message, or text message. The intent behind such attacks is to deceive the recipient into revealing sensitive information, which can then be used to commit fraud, identity theft, or other forms of cybercrime.
Types of Phishing Attacks
The world of phishing is not limited to just one type; it has several forms, each with its own unique characteristics and methods of operation. Four common types of phishing attacks are Email Phishing, Spear Phishing, Vishing, and Whaling. While they vary in their approach, from traditional email phishing to more innovative strategies like spear phishing and smishing, all share a common objective: the theft of your personal information.
Identifying and Avoiding Phishing Scams
A phishing attack can be fatal to businesses that fail to implement essential safeguards. It impacts the bottom line and can potentially destroy a brand’s reputation and trust if news of a data breach becomes public. Being able to identify and avoid phishing scams is, therefore,
paramount to maintaining a secure and trustworthy business.
In the face of this threat, it’s crucial to remain vigilant daily. Continuously providing security awareness training ensures your sta� and executives never become targets. Awareness and education are two of the most e�ective weapons against phishing attacks.
Security Awareness Training with ResilientIT.
At ResilientIT, we understand cybersecurity’s importance and awareness’s role in combating phishing attacks. Our company provides security awareness training through our training software, KNOWBE4, which boasts the world’s most extensive security training library. Our training programs are designed to equip your team with the knowledge and skills to recognise
and respond to various cyber threats.
By engaging in our managed simulated phishing and training awareness campaigns, you gain the tools to address security issues within your organisation effectively. We offer tailored solutions to meet your unique needs and ensure you are well-equipped to maintain a robust cybersecurity posture.
Contact us today to arrange your training and fortify your defenses against the ever-evolving threat of phishing attacks.
For more information, visit our website at www.resilientit.co.nz
ISO27001:2022: What do the updates mean for you?
ISO/IEC 27001:2022 Update: What are the main changes and what does this mean for you? This year, the ISO27001 standard saw its first significant update since 2013. What, however, do these changes mean for your organisation’s security? Why has ISO27001:2022 changed? At...
Webinar: ISO 27001: What can Kiwis learn from one of the leading standards for information security?
With the increase of businesses moving to data-driven solutions comes the need for the implementation of information security best practises. Cue, ISO 27001. ISO 27001 is a globally recognised international standard focussed on information security management that...